According to the different structures and scales of protected object networks, there are generally two kinds of system structures: secondary structure and tertiary structure. system structure 1, secondary structure The secondary structure is suitable for protecting a network with a simple topology structure. The system consists of an intrusion detection engine and a management console. The intrusion detection engine is a dedicated hardware device. It generally uses a 1U industrial host and can be installed on a standard rack. Its role is to capture the data transmitted in the network, detect attacks and issue real-time alarms, save the detected information for later inquiry and analysis. Hardware Configuration: The management console is a set of software that can be installed on the network administrator's host (Windows 2000/NT operating system). Its role is: configuration management of the engine, receive real-time alarms, query engine data. 2, three-tier structure The tertiary structure is suitable for protecting large and medium-sized networks. It consists of three parts: an intrusion detection engine, a center machine, and a management console. Large and medium-sized networks have complex topologies, geographical distribution, and large data traffic. Multiple engines are required to monitor the entire network. In this case, a special center machine was added to collect and save the data detected by each engine, perform secondary analysis, and provide the administrator with a comprehensive analysis report. The administrator's instructions can also be automatically delivered to each engine through the center machine to improve the management efficiency. The main function The intrusion detection system constantly monitors every connection that occurs in the network and faithfully records it in the database for administrators to query and analyze. The intrusion detection system captures all the data transmitted between the internal and external networks of the network in real time. Using protocol analysis and pattern matching methods, it can effectively identify various network attacks and anomalies, such as denial of service attacks, unauthorized access attempts, and pre-attack detection. . When an attack occurs, real-time alarms can be issued in various ways according to the administrator's configuration, such as notifying the administrator of the host, sending E-mail, notifying the firewall, and so on. For a serious network intrusion event, the intrusion detection engine can also directly send a blocking signal to cut off the connection where the attack occurs. Typical application plan This kind of network structure is relatively simple. Only a single engine needs to be installed to monitor the entire network. This type of network topology is complex and requires the installation of multiple engines for distributed detection. Conclusion The practice has proved that the above system integrates intrusion detection, network monitoring, real-time alarm and active defense functions, providing all-round protection for computer networks. It can be widely used in computer networks of government agencies, enterprises, schools, banks, and power companies. , is a faithful guardian of cyber security. Female Header,Female Header Pitch 2.54Mm,Smt Female Header,In-Line Patch Female Connector Shenzhen Jinyicheng Electronci Technology Co.,Ltd. , https://www.jycconnectors.com
1U chassis RPC-1100E
Multi-network port CPU card NORCO MB-3L-B
CPU PIII 1.0G
Memory 256M SDRAM
Hard disk 40G 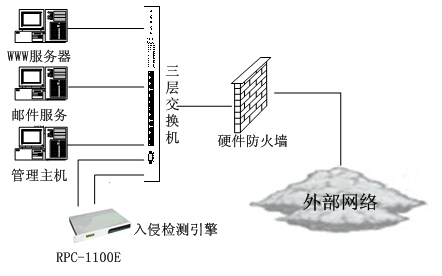
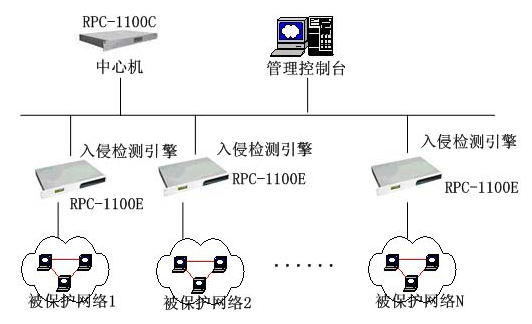
   Intrusion detection is a new generation of security technology following the "firewall" and "information encryption." It monitors events in computer systems or networks, analyzes them, looks for various intrusions that threaten network security, and alerts them in time.